In late 2019, I carried out an anonymous survey amongst AWS containers users. The survey focused on container security good practices and uptake of tooling in this space.
A word on the methodology: I put together an online survey using Typeform,
comprising 13 questions, four of which were Kubernetes-specific. I then posted the survey with a call for action to various fora including AWS/CNCF/Kubernetes Slack community channels, on Reddit in r/aws, discuss.kubernetes.io as well as word of mouth promotion, asking colleagues to invite their customers to participate. The survey opened on 2019-12-12 and was accessible until 2019-12-30.
The summary of the survey results is available as a PDF for download.
Welcome to the AWS container security survey 2019! This is an informal survey about container security practices, should take some 5 min. The survey is open until end of 2019 and I plan to publish the results on GitHub. Thanks for your time!
Note: if you’re interested in the raw data, check out the responses and results CSV files, respectively.
The questions of the survey were:
- How do you run your containers on AWS?
- Are you scanning your container images?
- Are you scanning containers at runtime?
- How are you managing sensitive data?
- Are you signing container images?
- How are you managing your supply chain?
- Are you using Kubernetes?
- Kubernetes: network policies
- Kubernetes: pod security policies
- Kubernetes: user management
- Kubernetes: pod-level IAM roles
- Any other security-related feature of AWS you’re using? Any container security tool?
- My role in the team/organization is …
In detail, the questions including context, options and completion rate were as follows:
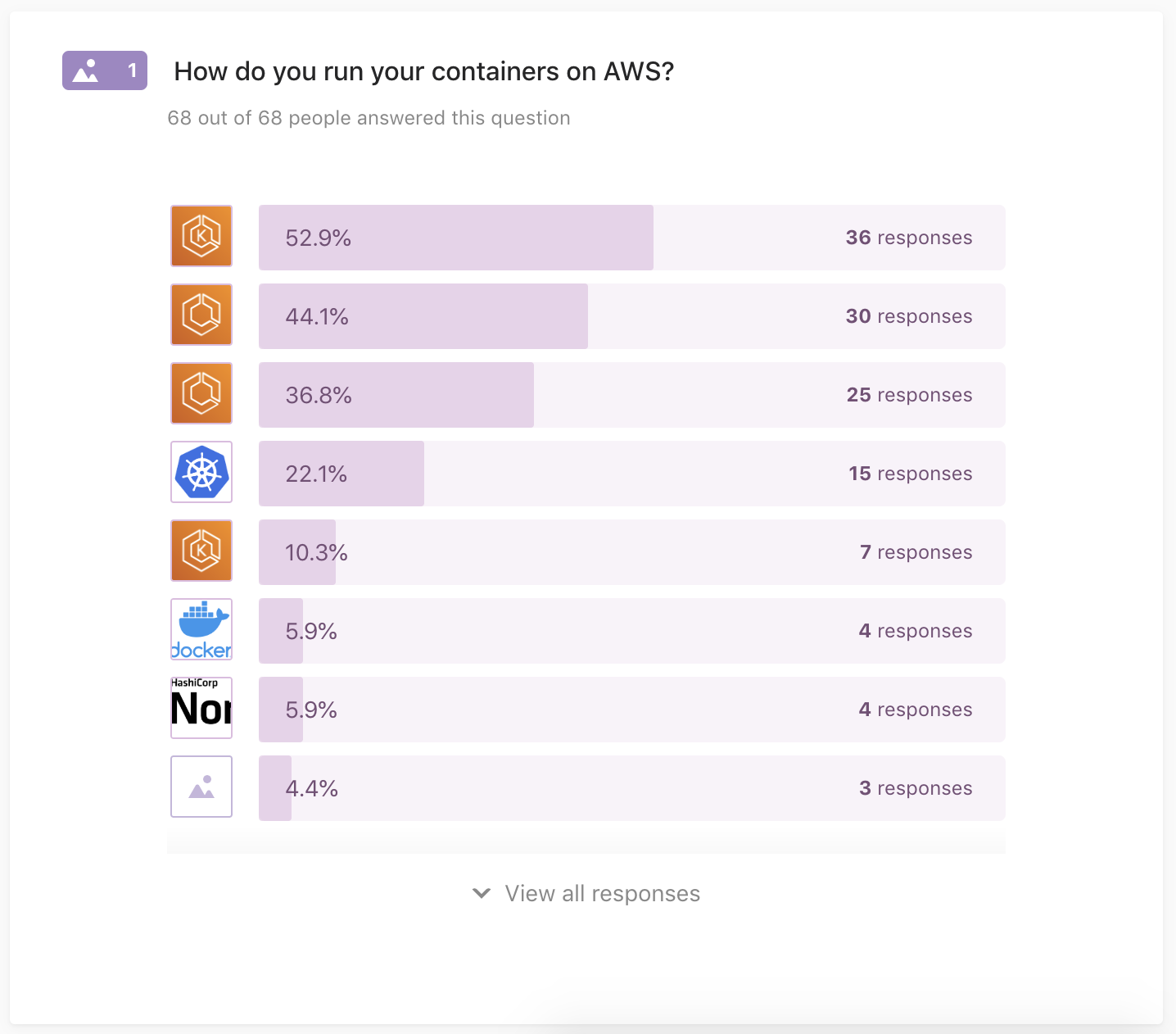
Q1: How do you run your containers on AWS?
68 out of 68 people answered this question
The container orchestrator & compute engine of choice, either what you’re already using in prod or plan to use:
- ECS on EC2
- ECS on Fargate
- EKS on EC2
- EKS on Fargate
- DIY Kubernetes (kops, etc.)
- HashiCorp Nomad
- Docker EE
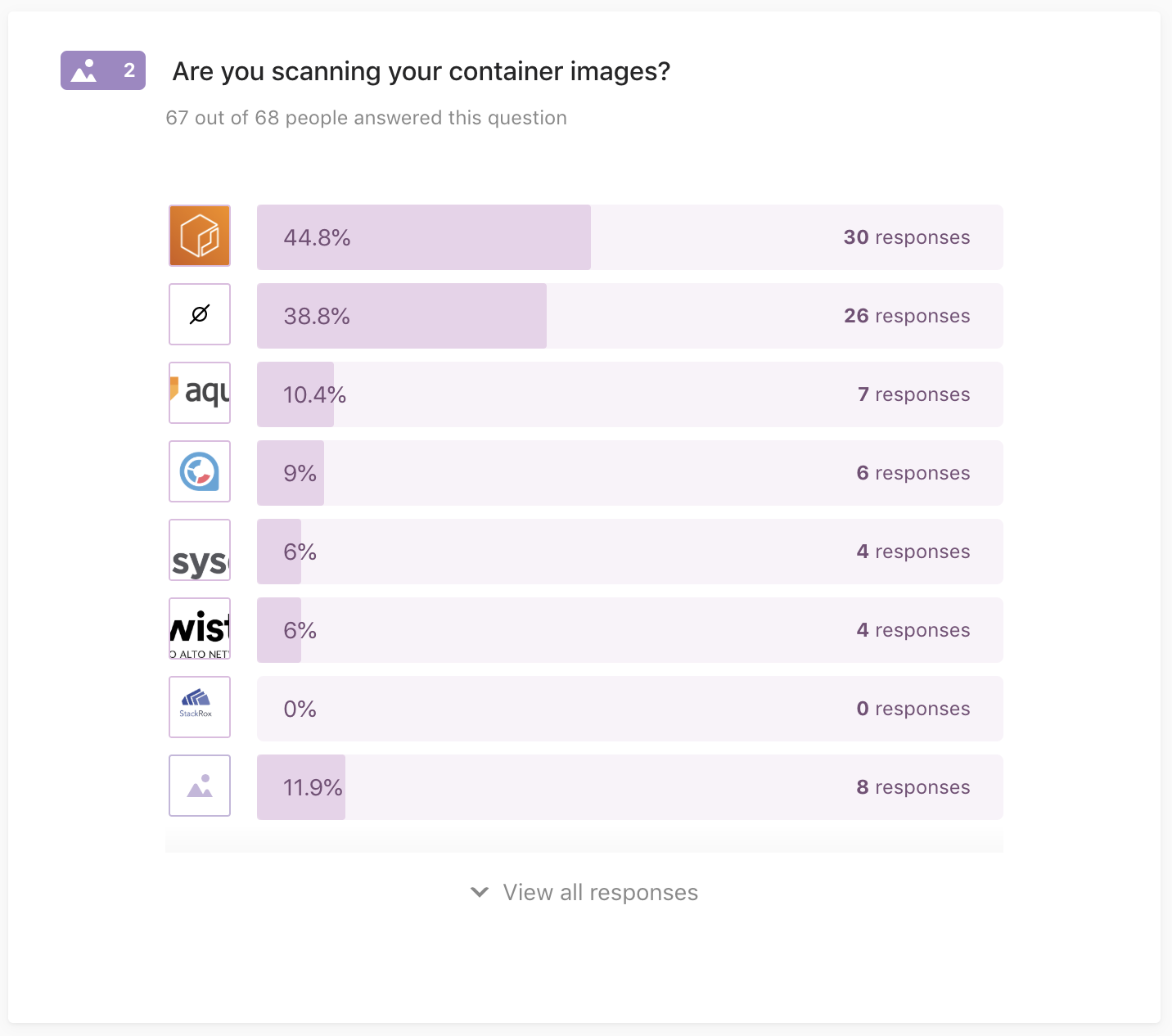
Q2: Are you scanning your container images?
67 out of 68 people answered this question
Performing static container image scanning, for example, as part of the build pipeline, using:
- Native ECR scanning
- DIY Clair
- Aqua Security
- StackRox
- Sysdig Secure
- Twistlock
- Nope, not scanning images (yet)
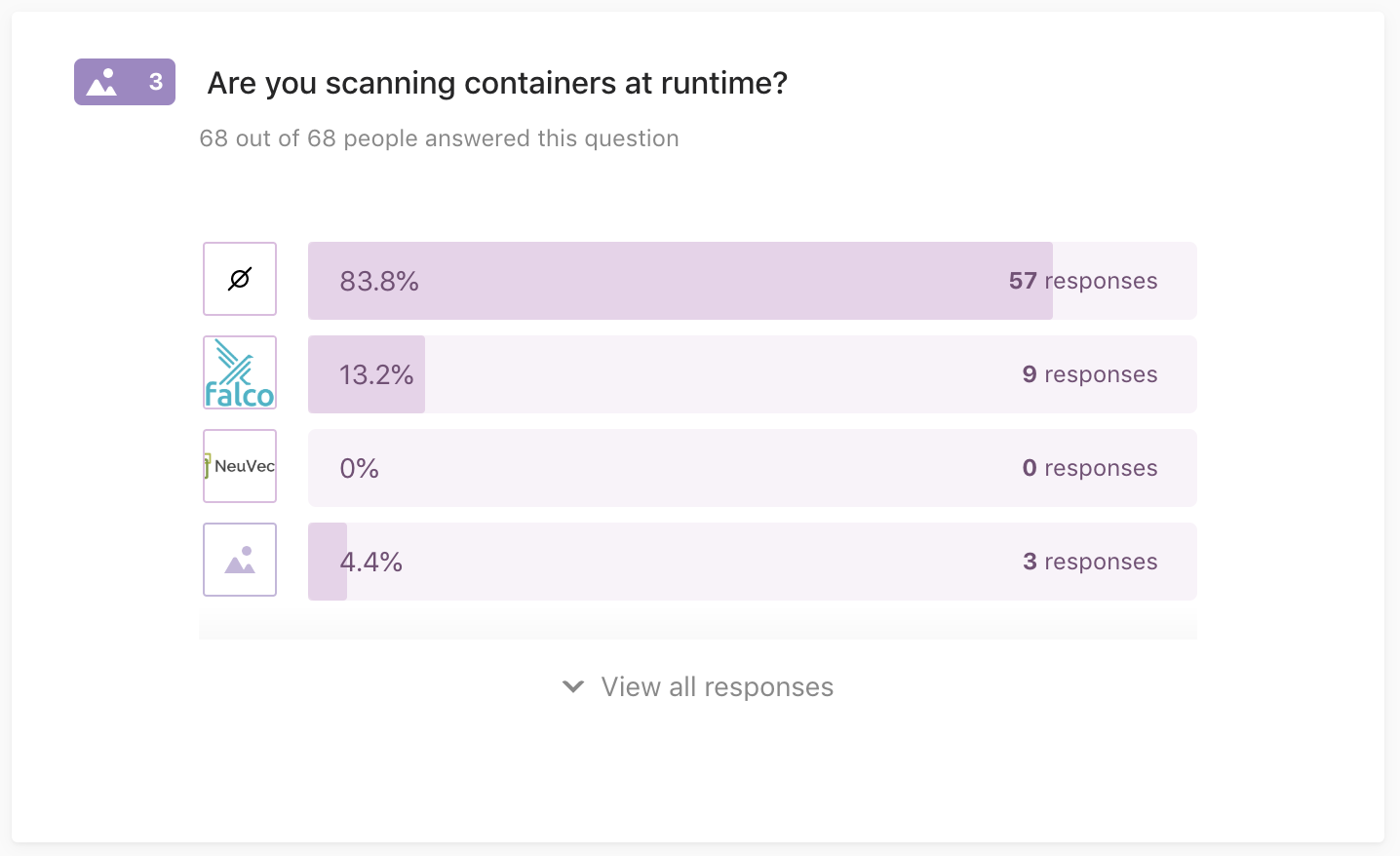
Q3: Are you scanning containers at runtime?
68 out of 68 people answered this question
Performing dynamic container scanning, as part of the container orchestrator, using:
- CNCF Falco
- NeuVector
- Nope, not scanning containers (yet)
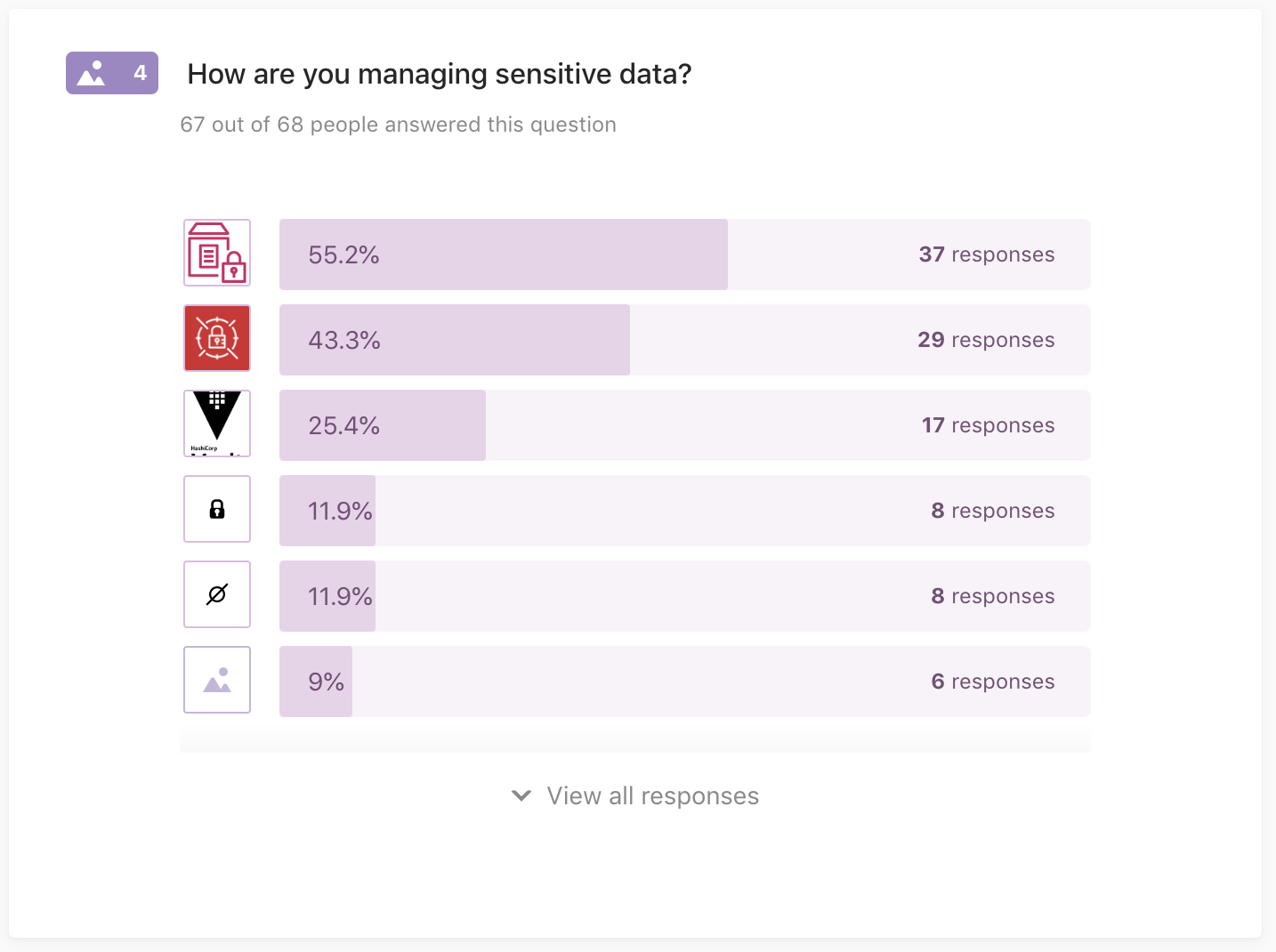
Q4: How are you managing sensitive data?
67 out of 68 people answered this question
Keeping sensitive data, such as passwords, API keys, etc. safe using:
- AWS Secrets Manager
- AWS Parameter Store
- HashiCorp Vault
- DIY encryption
- Nope, not encrypting sensitive data (yet)
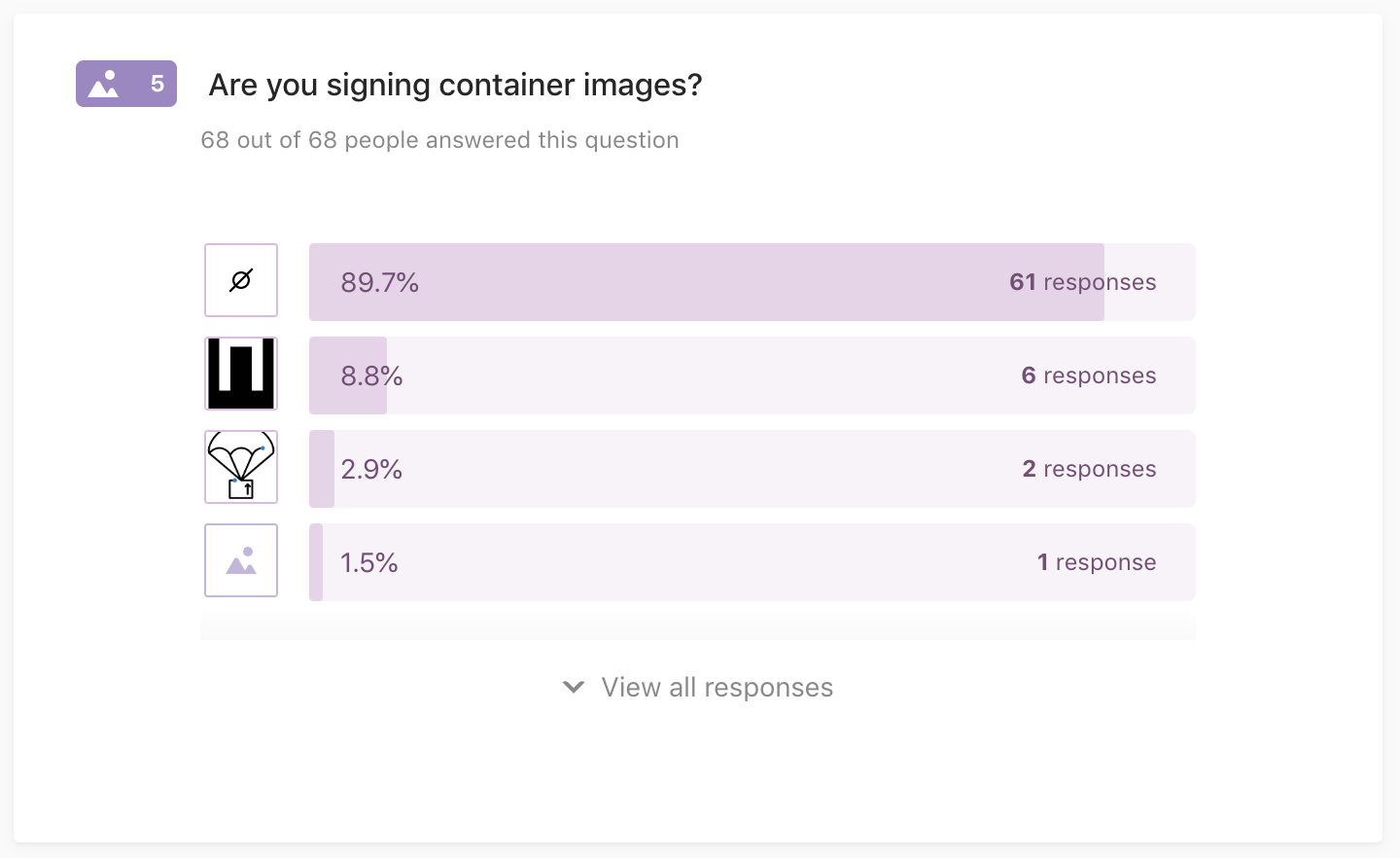
Q5: Are you signing container images?
68 out of 68 people answered this question
Signing container images cryptographically using:
- CNCF Notary
- CNCF TUF-based
- Nope, not signing my images (yet)
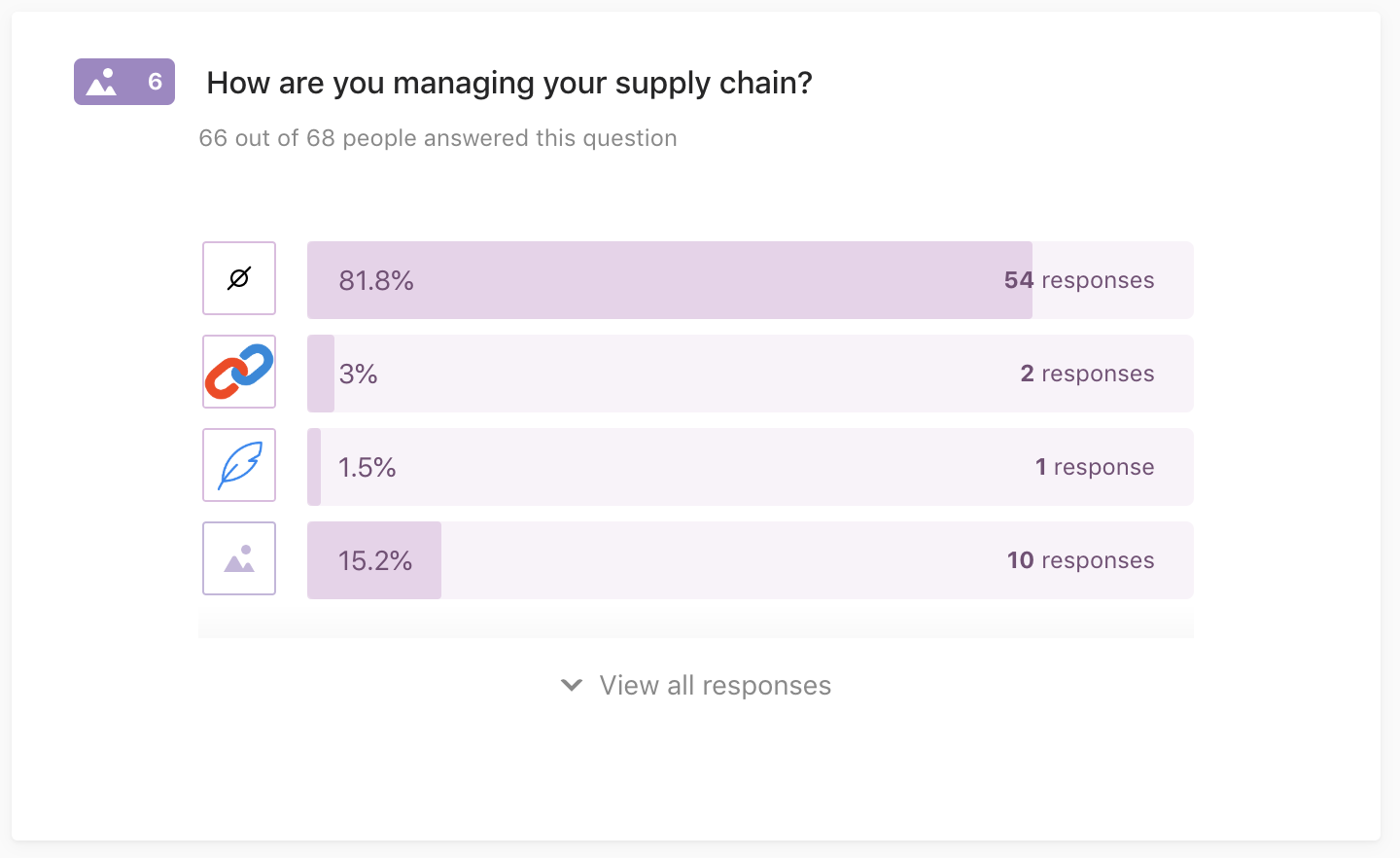
Q6: How are you managing your supply chain?
66 out of 68 people answered this question
The artefacts, such as container images, along the supply chain are managed using:
- CNCF in-toto
- Grafeas
- Nope, not managing my supply chain (yet)
Q7: Are you using Kubernetes?
68 out of 68 people answered this question
If the answer to Q7 was “Yes”, the following questions Q8 to Q11 were asked, additionally:
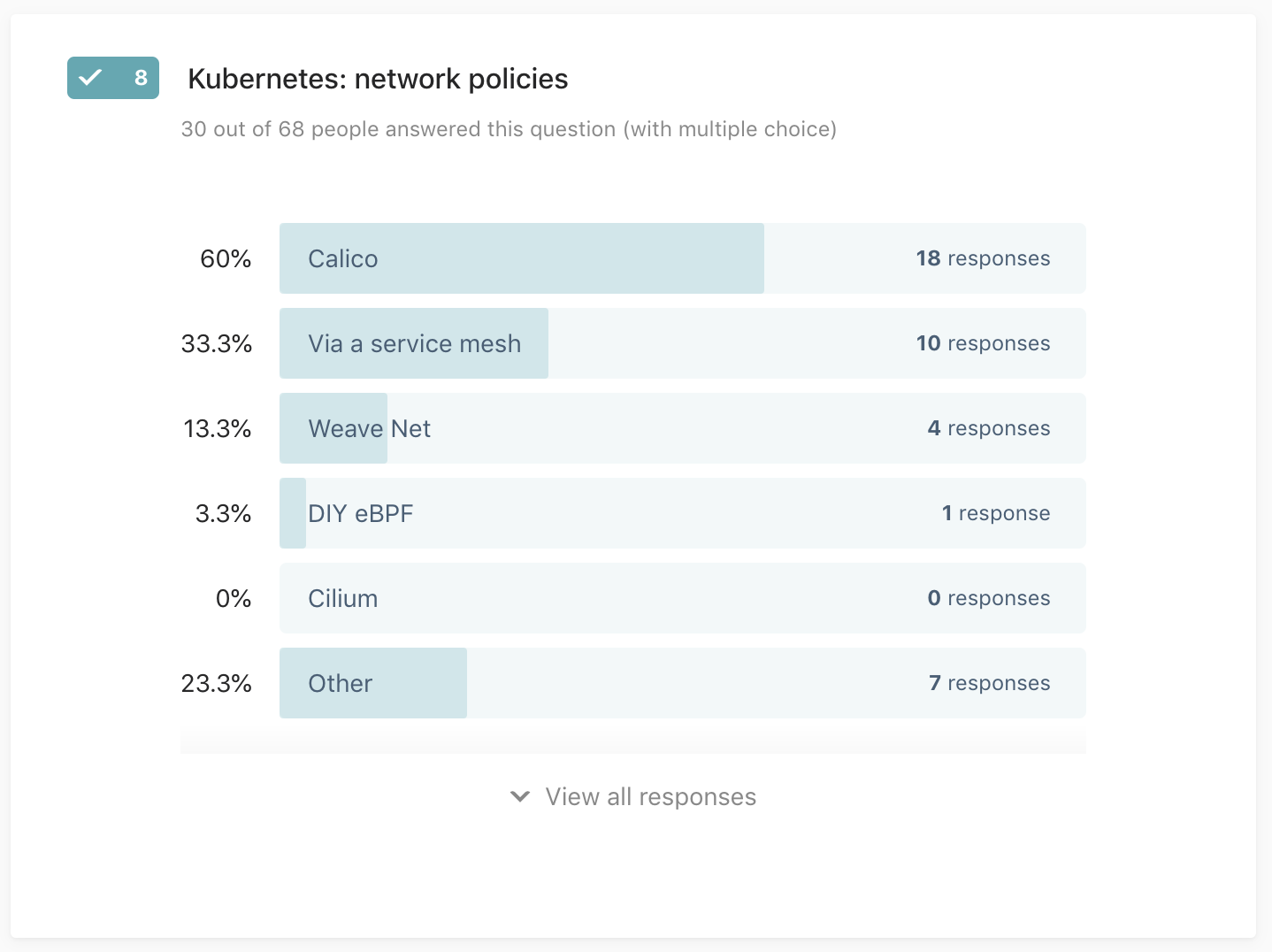
Q8: Kubernetes: network policies
30 out of 68 people answered this question (with multiple choice)
The artefacts, such as container images, along the supply chain are managed using:
- Weave Net
- Calico
- Cilium
- DIY eBPF
- Via a service mesh
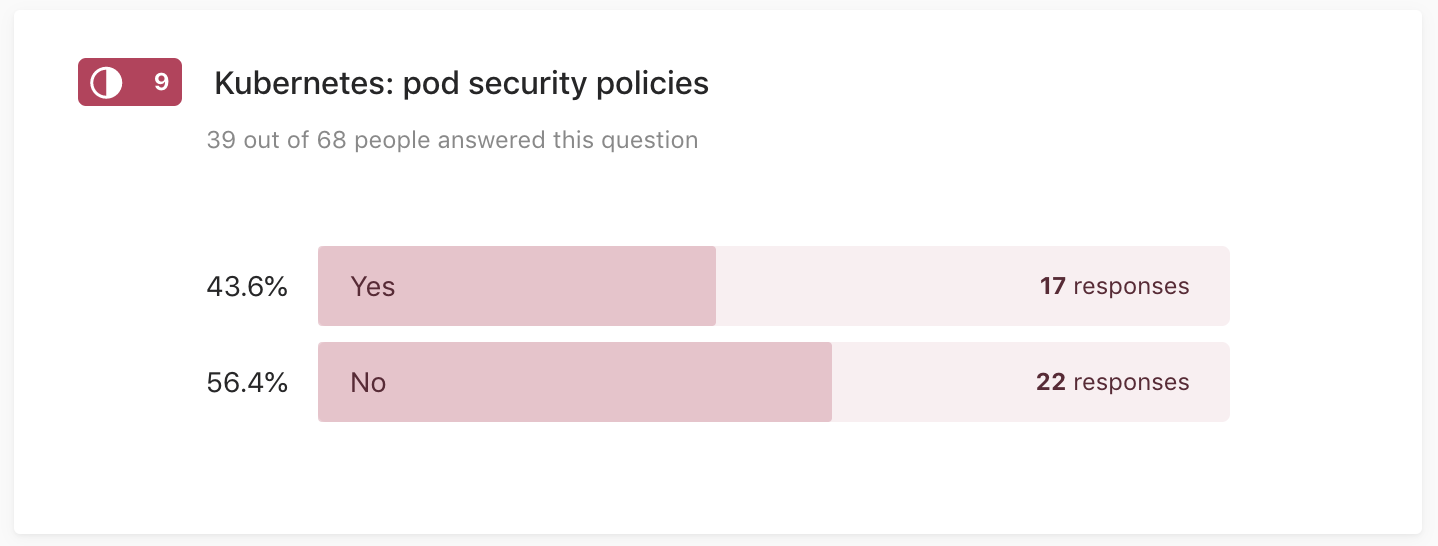
Q9: Kubernetes: pod security policies
39 out of 68 people answered this question
I am already using (or in the process of introducing) PSP.
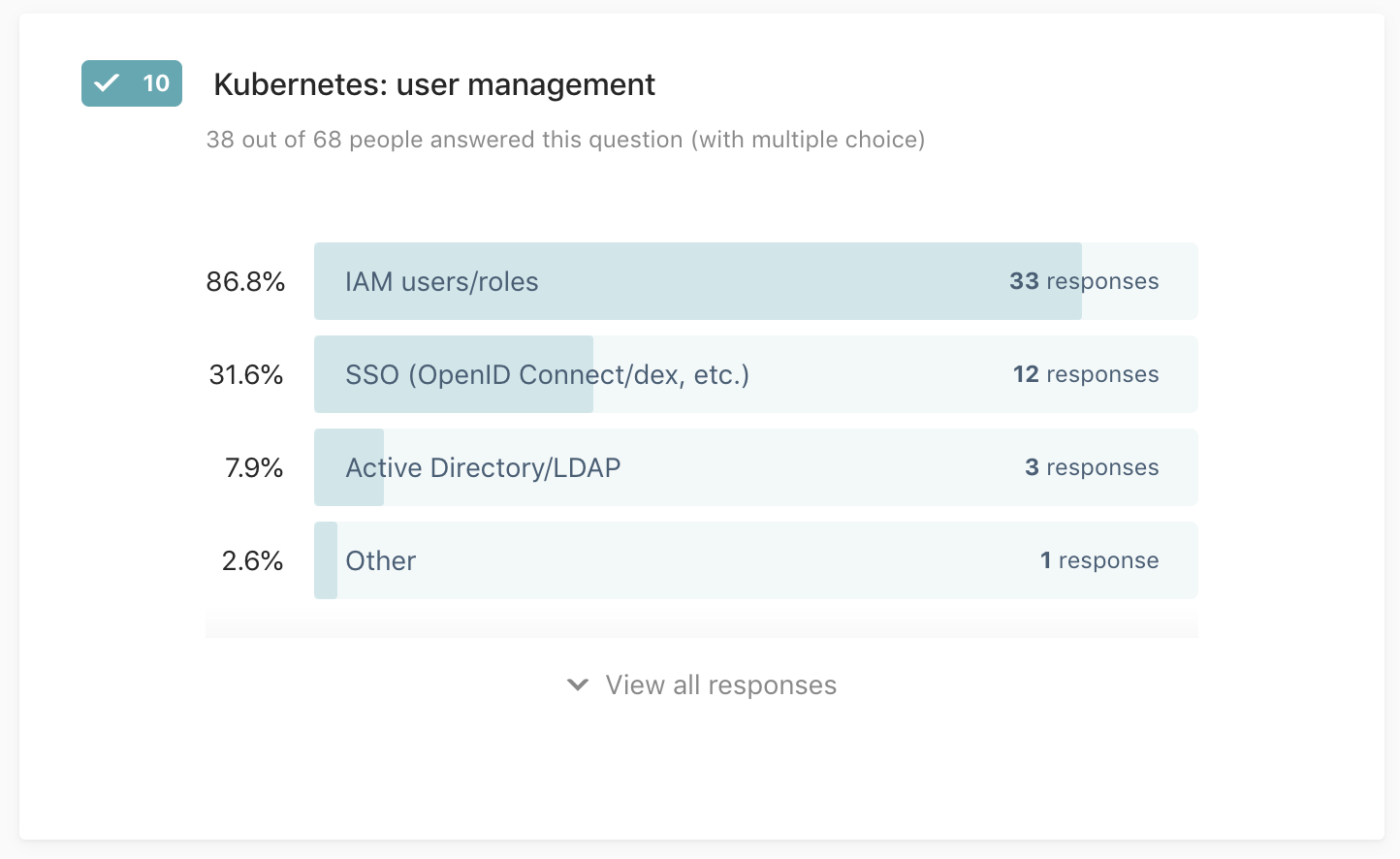
Q10: Kubernetes: user management
38 out of 68 people answered this question (with multiple choice)
To manage user identities I’m using:
- IAM users/roles
- Active Directory/LDAP
- SSO (OpenID Connect/dex, etc.)
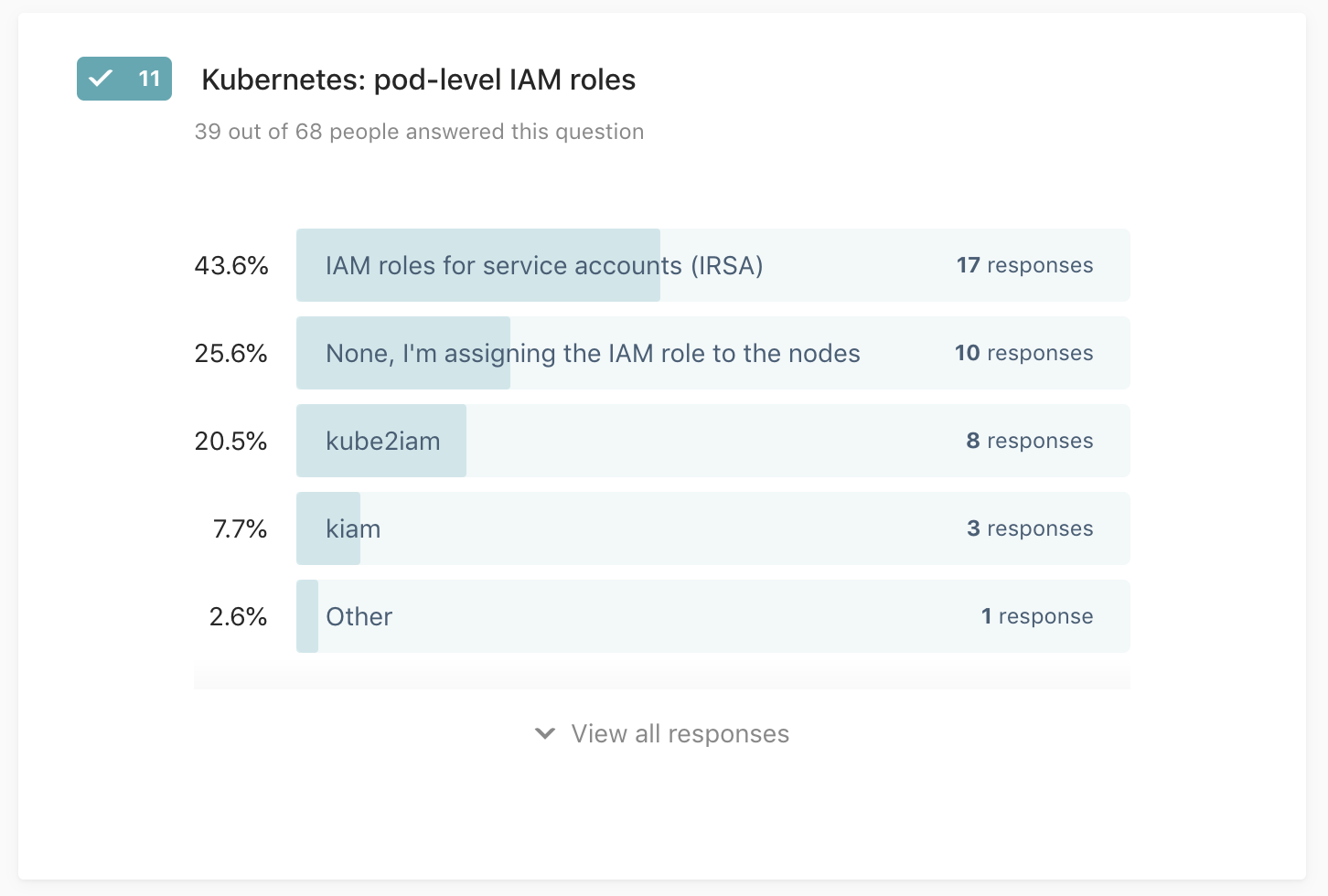
Q11: Kubernetes: pod-level IAM roles
39 out of 68 people answered this question
When using AWS services from apps running on Kubernetes, I’m using:
- IAM roles for service accounts
kube2iamkiam- None, I’m assigning the IAM role to the nodes
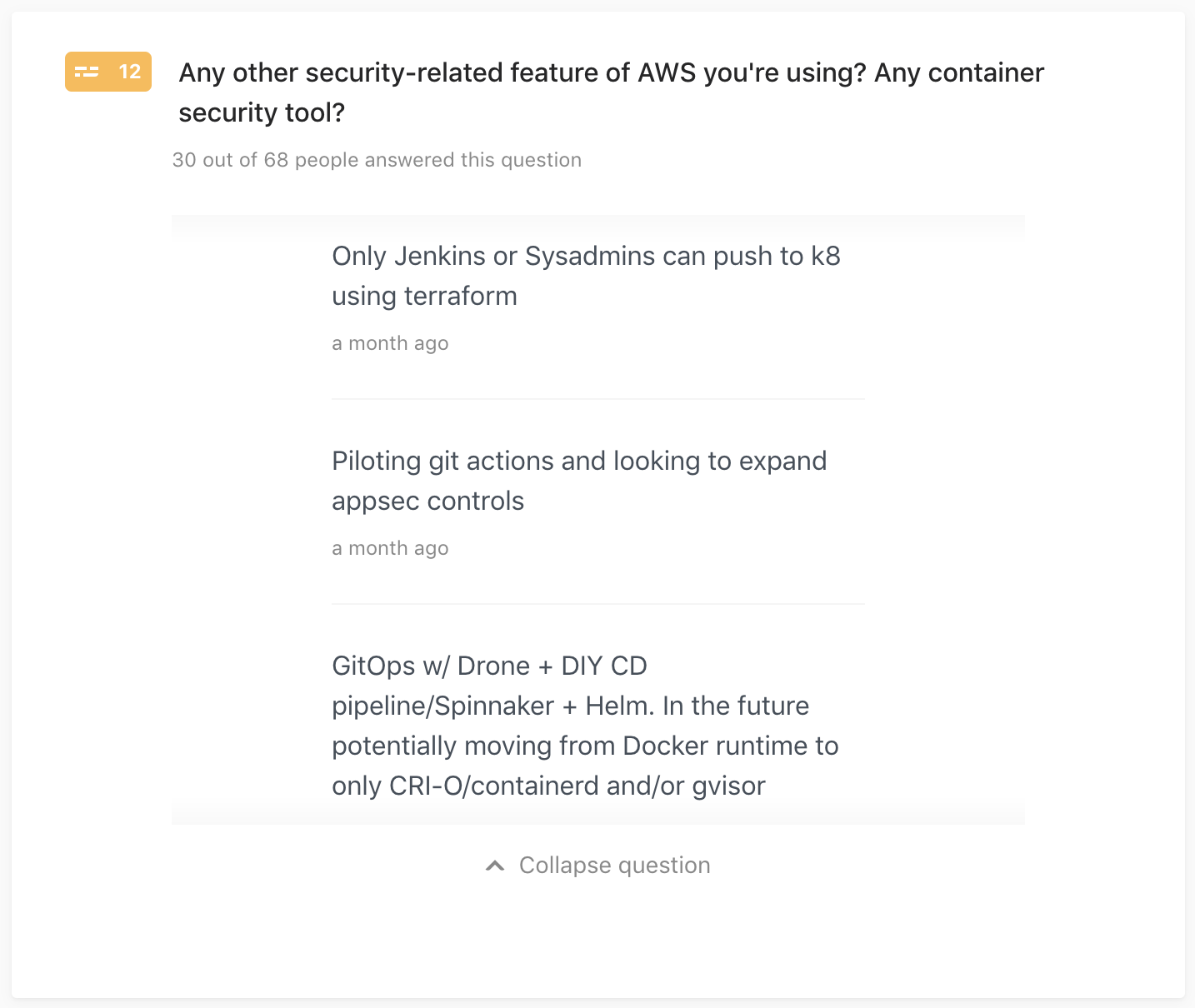
Q12: Any other security-related feature of AWS you’re using? Any container security tool?
This is a free-form comment, so feel free to share any other tool you’re
evaluating or already using. For example, Firecracker for multi-tenancy or
audit2rbac for generating RBAC roles or maybe you’re implementing GitOps
(such as Flux) to strengthen your security posture?
30 out of 68 people answered this question
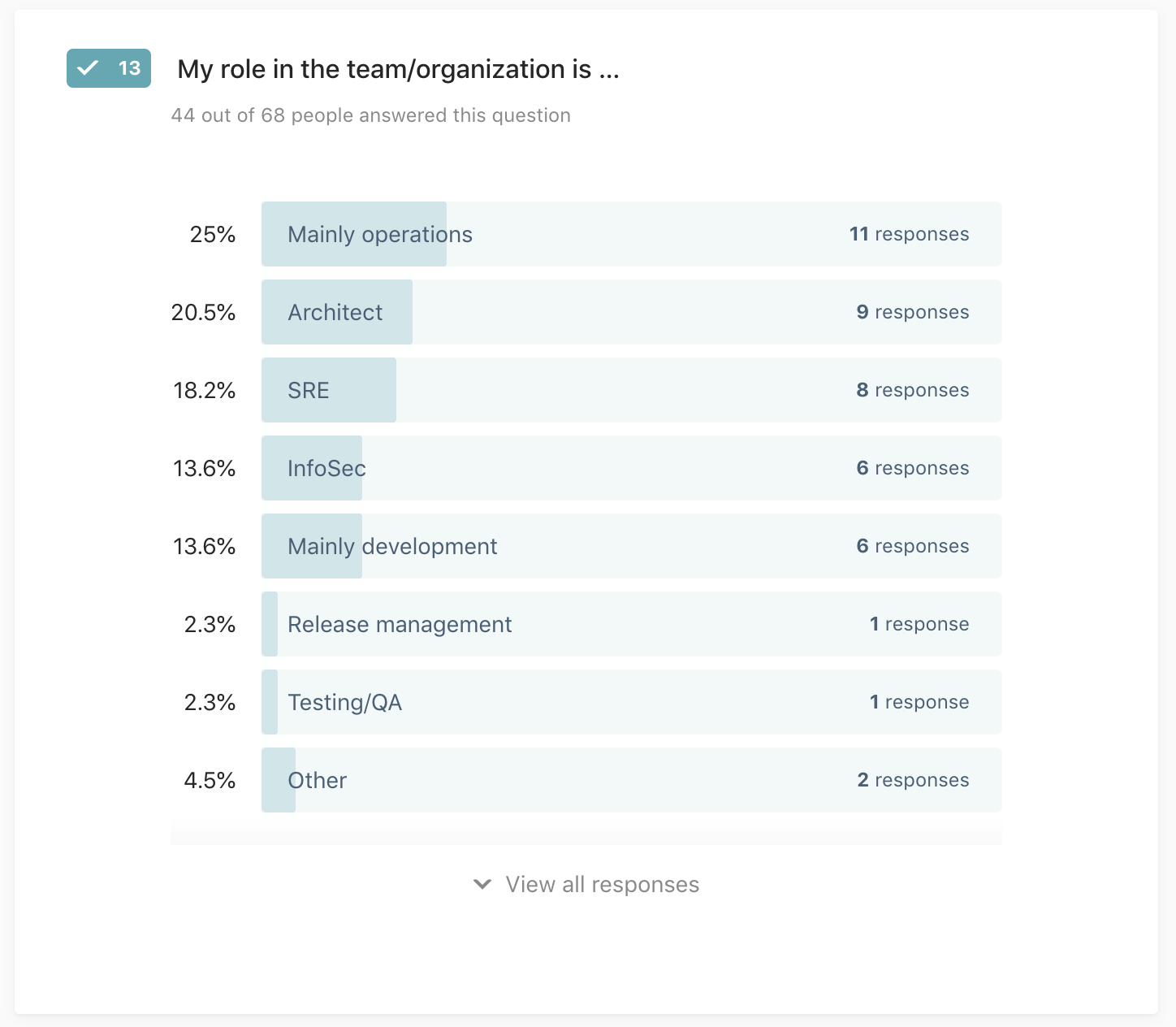
Q13: My role in the team/organization is …
44 out of 68 people answered this question
- Mainly operations
- Mainly development
- InfoSec
- SRE
- Release management
- Testing/QA
- Architect